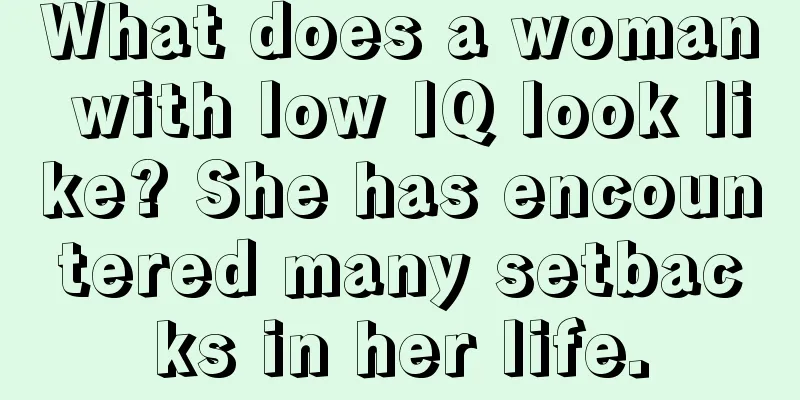Discussion on blockchain and QR code security authorization technology

|
This article describes a QR code device authorization solution based on blockchain technology. Here, we use the access control system of an enterprise as an example to explore the combination of QR code and blockchain to achieve an anonymous QR code access control authorization permission. In traditional access control systems, the management of access personnel is mainly through card swiping, fingerprint, iris, or manual authorization. The rapid development of QR code technology and the widespread popularity of mobile devices such as mobile phones have made the above solution possible. Visitors can make an appointment for a visit through their mobile phones or the Internet, and then get a temporary QR code authorization license image. They can then print this QR code on paper or save it on their mobile phones. When it reaches the access control device, the access control device can recognize this QR code to achieve visitor access authorization management. This is unattended. In this picture, the visitor has obtained the legal private key, public key and other key data through the blockchain, and the access control system only recognizes this information. Only with this information can it be possible to pass through the access control system, which creates the possibility of passing through the access control system completely anonymously. Author's note: Thanks to the enthusiastic help from the members of the BitNet community. Author: 642 |
<<: FamilyMart's 3,000 convenience stores have adopted BitoEX Bitcoin wallet
>>: The global mobile workforce is growing, and blockchain technology is helping business management
Recommend
Are people with full foreheads more likely to succeed than others? People with full foreheads have better luck.
1. People with full foreheads are smart People wi...
What kind of palm is the most blessed for boys?
We all say that we can tell a person’s fortune by...
What does a mole on the arm mean?
What does a mole on the arm mean? If you have a m...
The face of great wealth
Some people are born with a silver spoon in their...
Analysis: What kind of palmistry can help one become an official
In the ideology of the Chinese nation, being an o...
The fate of a man with straight eyebrows What is the personality of a man with straight eyebrows
Eyebrows play a very important decorative role in...
Analysis: Bitcoin investors hold onto their coins, while miners hoard them
According to Cryptopotato on August 31, Bitcoin m...
What crow's feet reveal about your love life
What crow's feet reveal about your love life ...
A man who always smiles and is very friendly
Some people always look very cold and indifferent...
Bitcoin has gone crazy again, breaking through 8,600 to set a new all-time high!
In just a few days, the price of Bitcoin soared f...
Are women with thick earlobes happy after marriage?
No matter who you are, you all hope that you can ...
Revealing what kind of face is the best and most prosperous for a woman
I believe that everyone hopes to be lucky enough ...
A complete analysis of nasolabial folds
Not everyone has nasolabial folds, so what do naso...
Which palmistry shows that people are generous with money?
Based on their attitude towards money, people can...
The first Global Internet Finance Leaders Summit concluded successfully, with blockchain becoming the focus
On December 20 , the 2015 First Global Internet F...